Introduction to BGP Blackholing
Introduction to BGP Blackholing
BGP blackholing is a way for networks to deal with bad traffic. When lots of data that's not good comes in, this method helps by sending it nowhere, like into a black hole in space. It makes sure the rest of the network runs smooth without getting slowed down by these unwanted bits and pieces.
Special rules within BGP help different internet parts communicate. Harmful data is quickly dropped to prevent damage and save space for real information flow.
Understanding BGP Protocol
The Border Gateway Protocol (BGP) plays a crucial role in how data moves around the internet. It allows networks to share routes with each other, ensuring information finds the quickest path between points A and B. Think of it like a map that constantly updates itself with the best roads for your journey.
Every time you visit a website or send an email, BGP is at work behind the scenes, guiding those bits of data across various networks to reach their destination efficiently. However, this system isn't perfect; it relies on trust among network operators not to spread incorrect route information—whether by mistake or malicious intent—which can lead traffic astray or into dead ends. Despite these challenges, understanding BGP's mechanics remains essential for anyone involved in managing network infrastructure because of its fundamental role in global communications today.
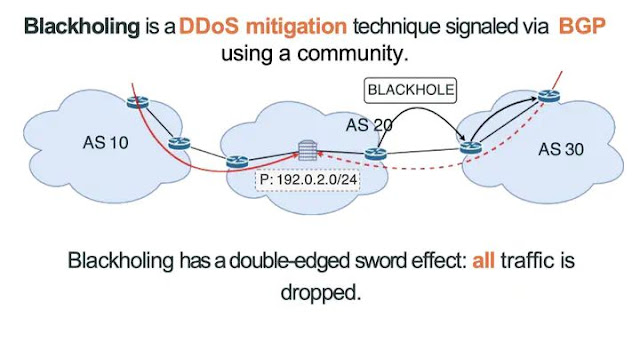
Basics of BGP Blackholing
BGP Blackholing acts as a shield against unwanted data floods by directing bad traffic into a 'black hole' where it can't do harm. Networks use this method to protect servers and vital systems from being overwhelmed during an attack. Here's how it works: network operators flag harmful incoming data with a specific marker.
This tells routers in the path to send this bad traffic away from critical resources, effectively isolating it. For efficiency, BGP Blackholing needs precise setup on routers throughout the internet. It allows providers more control over their networks without affecting good user connections since only marked data gets redirected or dropped.
Bear in mind that for BGP Blackholing to work well across different regions and systems, coordination among various internet service providers is crucial. They must agree on common signals for identifying and managing such hostile flows of information efficiently while ensuring legitimate access remains unaffected.
Role of BGP Communities
BGP Communities play a vital role in managing network traffic by allowing operators to tag routes with specific handling instructions. These tags, part of the BGP Update Message Path Attribute, guide other networks on how to process certain paths. By setting values in the Communities attribute, networks can control route preferences and distribution — signaling how to accept or prefer a route without altering base attributes.
Originally outlined in RFC1997 as four-octet values with minimal constraints, this system evolved through RFC4360 into Extended Communities. This expansion introduced type flags for more nuanced controls and allowed precise policy implementations across different networks using two octets for targeting policies at specified network segments. One significant application is defending against DDOS attacks via Remotely Triggered Black Holes (RFC5635), directing peers to drop attack traffic close to its source while maintaining flow towards legitimate destinations.
Essentially, BGP communities facilitate complex routing decisions that balance load distribution and enhance security measures across sprawling internet landscapes.
Implementing BGP Blackholing
For network security, BGP blackholing serves as a critical method to protect against attacks. It works by signaling neighbors in other networks (ASes) to ignore traffic going toward a specific IP prefix under attack. This process effectively blocks harmful data before it can damage the victim's infrastructure.
Internet Exchange Points (IXPs), where many ASes gather, are ideal for spreading these signals efficiently across multiple networks. However, not all attempts at implementing RTBH filtering succeed. Some peers may reject these routes based on their local policies, letting unwanted traffic through.
Studies reveal that acceptance and effectiveness vary greatly with different IP prefix lengths; /24 prefixes often see notable yet imperfect mitigation rates. The reality is more complex than anticipated due mainly to configuration errors—specifically failing to accept crucial prefixes—a key factor behind less effective blackholing efforts.
Benefits of Using Blackholing
Using BGP blackholing brings key benefits to network security. It helps by making bad traffic go nowhere, just like a hole that swallows whatever falls into it. This means attacks don't hit their target but are instead dropped, keeping services running smooth and safe for users.
One major gain is less downtime during an attack; sites stay up when they might have crashed under the pressure of harmful data floods otherwise. Another point is cost saving. With this method in place, there's no need for extra hardware or software tools aimed at stopping these threats because the blackhole does the job efficiently on its own without added expenses.
Lastly, setting it up can be quick which allows networks to react fast against sudden cyber threats ensuring minimal harm done and keeping both user trust and service quality high.
Challenges in Deployment
Deploying BGP blackholing presents its own set of challenges. A key concern is the limited use in blocking prefix squatting incidents, as our analysis shows. This technique, while not often applied to restrict access to content by clients, can serve this purpose effectively when needed.
For example, network operators have used it to block harmful actors like port scanners from accessing server contents rather than targeting victims directly. Another critical aspect involves using RTBH for censorship purposes—blocking traffic towards IP addresses that host undesired content. Herein lies a significant advantage: simplicity over traditional methods such as access control lists (ACLs).
With RTBH, instead of configuring ACLs on every router individually—an operational burden—a single router can manage the master file and communicate blackhole routes through BGP with peers. Our investigation draws upon data collected over three months at a major European Internet Exchange Point (IXP) offering remotely triggered blackholing services predominantly focused on IPv4 due to its prevalence in both traffic and RTBH events observed during this period. Despite advancements in DDoS mitigation technologies matching or even surpassing attack growth rates and magnitudes respectively; understanding their deployment success remains intricate but crucial for refining future defense mechanisms against such threats.
Best Practices for Security
For better security, NIST advises on steps that fit easily with most BGP routers. They focus on the current protocol, Version 4. Big changes to BGP could lead to issues as new ways might not work well with old ones.
Their tips aim to make things safer without needing a big overhaul. Key advice includes setting up access control lists. This helps in deciding who gets through and who doesn't.
Also important is controlling what networks or blocks get announced. This way, one can keep unwelcome traffic out. Filtering plays a huge role too; it sorts good from bad data coming in or going out.
Moreover, allowing connection only via port 179 adds an extra layer of safety by limiting unwanted access attempts. All these suggest practical steps within existing systems for tightening security around network exchanges.
Monitoring and Managing Traffic
In managing web traffic, experts track and guide data flow to ensure smooth network function. They use tools that analyze patterns. This identifies high-traffic times or potential threats like DDoS attacks.
For effective oversight, they might redirect harmful traffic away from key resources using BGP blackholing techniques. It's a method where problematic IP addresses are sent into a "black hole," off the main network pathway, so normal operations continue undisturbed. Monitoring also involves checking for any unusual activity which could signal an attack or system issue needing immediate attention.
Regular updates and adjustments keep this process sharp against evolving cyber threats. Professionals stay informed through continuous learning about new technologies and tactics in digital security defense. This proactive approach helps maintain stable internet access for users while protecting sensitive information from unauthorized breaches—a critical balance in today’s connected world.
Evaluating Impact on Network
When looking at the impact on networks, one sees that mishaps, be they by chance or purposeful acts, often shake up online safety. A deep dive into data helps gauge how wide and big such events are worldwide. It sheds light on just how much these issues mess with our digital world's peace.
There exist methods to help curb these risks yet their use isn't foolproof. The globe's internet doesn't care for borders; it connects us all in unseen ways. This reality brings both a challenge and an opportunity for those making policies aimed at safer connections across countries.
The said report hands them solid steps toward better security within this boundless network space. In essence, each incident tallies up to broader implications affecting more than just local nets but also stirring global policy talks towards safeguarding digital realms against disruptions.
BGP Blackholing plays a key role in keeping networks safe. It helps by stopping bad data from moving around the web. This method acts like a guard, directing harmful traffic into a void where it can do no harm to vital online places or info.
For companies big and small, learning how BGP Blackholing works is wise. It's one of many tools that make sure our use of the internet stays smooth and secure. Thus, embracing this technique means taking a big step toward safer digital spaces for all.