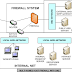
Firewall Standard Zones and Configurations
Lets talk about the security Zone in the enterprise network or you can say that implementing the Security Zone in the university that approach to firewall configuration and deployment. These “Security Zones” are implemented as rule-sets on University firewalls.
 |
| Fig 1.1- Standard Firewall Zones |
Each firewall will provide multiple “Security Zones” to implement specific security controls for each zone. Default sets of “Security Zones” are created during the implementation of each University firewall as follows:
- Workstation Zone
- Server Zone
- DMZ Zone
CSSD defines these “Security Zones” to be implemented for each firewall as follows:
- Workstation Zone – The Workstation zone is designed to protect a University Unit’s workstations, network printers, and other local network devices (inside the firewall) from all other zones. Access to this zone from all other zones is restricted and controlled
- Server Zone – The Server zone is designed to protect a University Unit’s critical infrastructure such as domain controllers, file, print, intranet (internal web applications), application, and database servers. Access to this zone is limited to the Unit’s Workstation Zone.
- DMZ Zone – The DMZ zone is designed to protect any server that is accessed by a broad audience. An example of this is a web server that is accessed by users from around the world. This zone acts as a protective layer between a University Unit’s workstations and servers. Only necessary ports are allowed inbound to this zone. Additionally, the Unit’s Workstation and Server zones are allowed to access the DMZ zone.
- Other Zones – Other Zones are specialised zones within a department. These zones are created on an as needed basis. Other zones typically follow the same access controls as workstation zones but may very according to needs. Examples of other zones are Labs, Classrooms, Development, Database, etc.
- Exceptions to any zone can be created with CSSD Security approval in accordance to the standards presented in this document.
Standard Firewall Configuration
- All physical network interfaces or VLAN interfaces will be configured with static IP addresses.
- Each physical firewall will be configured to support multiple virtual firewalls. Each virtual firewall has its own routing information, its own set of IP addresses, its own firewall policies, etc. through the use of partitions.
- Serial port access will be enabled on each physical firewall to allow local console management. A unique secure password will be assigned to each physical firewall for local console management.
- All rule-sets, rules, host groups and service groups will have a complete description (ex. the “VNC” service group description should be “VNC remote control application”, and describe the port and protocol “tcp5900”).
- Host groups will be defined as local to each firewall. Host groups that are used across multiple firewalls will be defined as global. Local firewall host group names will be identified using mixed case characters. Global firewall host group names will be identified using all upper case characters. When a Host groups that are converted from local to Global Group they will be modified to upper case.
- Service groups will be defined as global to all firewalls. Service groups that will be utilized for only one firewall will be defined as local to that firewall. Local firewall service group names will be identified using mixed case characters. Global firewall service group names will be identified using all upper case characters.
- All firewalls will be assigned a local console rule-set (“firewall”) and an administrative zone rule-set (“administrative zone”).
Firewall Rule-Sets
- Rule-sets will be defined for each “Security Zone” (Workstation Zone, Server Zone, DMZ Zone) as needed. Multiple rule-sets may be defined for each “Security Zone”.
- The system generated “firewall” rule-set will be assigned to the “local” interface for each firewall. The system generated “administrative zone” will be assigned to one of the network “etherX” interfaces for each firewalls.
Workstation Zone Rule-Sets
 |
| Fig 1.3- Workstation Zone Rule Sets |
 |
| Fig 1.4- Server Zone Set Rule |
 |
| Fig 1.5- DMZ Zone Set Rule |
Like us on Facebook : Networks Baseline on Facebook
Subscribe us on Youtube: Youtube Subscription for Videos !