Denial-of-Service (DoS) attack
What is Denial-of-Service (DoS) attack?
Today I am going to talk about the DDOS attack. As you know so many attacks happened these days which targets specified users or machines or organisations by sending the malicious content. Attackers know that they can be chased so that probably attack from the multiple location so that they cant be traceable. Various vendors in the markets giving various names to these types of attacks like Land attack, Ping of Death, Smurf attack, Zombie attack or many other names.
First we would like to talk about what this Denial-of-Service (DoS) attack is.
A Denial-of-Service (DoS) attack is an outbreak and meant to shut down an appliance or computer network, making it unreachable to its anticipated or dedicated users. DoS attacks achieve this by overflowing the objective or flooded with traffic, or transfer it evidence that causes a crash in the network or computers. In both instances, the DoS attack divests genuine users which actually wants to receive the data i.e. employees or so called members of the facility or resource they expected.
Preys of DoS attacks frequently target web servers or application servers of high profile administrations such as IT/ITs, banking, commerce, and media companies, or government and trade organizations. Though DoS attacks do not typically result in the stealing or loss of significant information or other properties, they can cost the victim a great deal of time and money to handle.
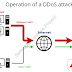
 |
| Fig 1.1- DDOS Attacks |
There are two general methods of DoS attacks: overflowing services or crashing services. Flood outbreaks occur when the system obtains too much traffic for the server to buffer, producing them to slow down and finally stop. Popular flood attacks include:
- Buffer overflow attacks – the most common DoS attack. The concept is to send beyond traffic to a network address than the programmers have built the system to grip. It includes the attacks listed below, in addition to others that are planned to manipulate bugs specific to certain applications or networks
- ICMP flood – influences misconfigured network devices by transfer spoofed packets that ping every workstation on the aimed network, instead of just one specific appliance. The network is then generated to magnify the traffic. This attack is also identified as the smurf attack or ping of death.
- SYN flood – sends a request to connect to a server, but never accomplishes the grip Continues until all open ports are flooded with requests and none are available for authentic users to connect to.
Other DoS attacks simply exploit weaknesses that cause the target system or service to crack. In these attacks, input is directed that takes benefit of bugs in the target that successively crash or severely undermine the system, so that it can’t be retrieved or used.
HTTP flood: An HTTP flood is another type of Layer 7 application bout that uses botnets, and often referred to as a “zombie army.” In this type of attack, normal GET and POST requests flood a web server or application. The server is flooded with requests and may shut down. These attacks can be particularly difficult to detect because they appear as perfectly valid traffic.
An additional type of DoS attack is the Distributed Denial of Service (DDoS) attack. A DDoS outbreak occurs when numerous systems orchestrate a harmonized DoS attack to a single aim. The essential change is that instead of being condemned from one location, the target is condemned from many locations at once. The dispersal of hosts that defines a DDoS provide the invader numerous advantages:
- He can leverage the bigger volume of machine to execute a completely disruptive attack
- The location of the attack is challenging to detect due to the random distribution of attacking systems (often worldwide)
- It is additional difficult to shut down multiple gears than one
- The true condemning party is very difficult to identify, as they are masked behind many (mostly compromised) systems
Current security machineries have developed mechanisms to defend against most forms of DoS bouts, but due to the unique features of DDoS, it is still observed as a raised threat and is of advanced concern to administrations that terror being targeted by such an bout.