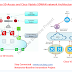
Cisco SD-Access Vs Cisco SD-WAN
Today I am
going to talk about the difference between cisco SD-Access and the SD-WAN. Both
are the ways to approach SDN terminology by taking DNA architecture. SD-Access as name suggested Software defined Access for changing the architecture of the
LAN networks while SD-WAN as software defined WAN which can automate and may be
next generation networks over the MPLS/VPLS. MPLS is still have a hold through
the service provider end, but using the SD-WAN will get rid of the control from
the service provider.
SD-Access
SD-Access has the components like DNA-Center which acts as a controller for control plane
and while data plane is still with the devices in the network. Make sure you
understand the difference between the DNA and DNA-Center.
DNA is an
architecture while DNA-Center is the controller in that architecture. The other
main component is Cisco ISE. Cisco ISE as already discussed in my previous articles
is used for authentication for the users in the network.
As I said
that the architecture changes, it means you can integrate the AD infrastructure
with Cisco ISE and Cisco ISE will feed the user authentication information with DNA-Center
Then policies will be pushed to the devices on the bases of the access information
that is fed to the Cisco ISE appliance.
The Network
work in the LAN based on the username and VXLAN tunnels created from source
port from the switch to the destination port. Now VLAN has no relevance in the
network but you can map existing VLANs with the SGT’s in the network as Cisco ISE will get the feed on the basis of the SGT’s.
Fig 1.1- SD-Access and SDWAN
|
SD-WAN
Similarly
for the SD-WAN Viptela architecture, there are three controllers which can be
on the cloud or on-prem deployment and can have the control plane. All devices
in the SD-WAN architecture works on the zero trust model and to maintain the
trust between them they need to create the DTLS/TLS tunnels and exchange the
certificates which are preloaded on the devices.
Make sure
you understand the traffic routed to the controller which is in the cloud
generally is only the control plane traffic. The End devices can be connected
for the data plane traffic over the secured IPSEC/GRE tunnels.
SD-WAN is
basically a application aware network and choose path on the based parameters
like SLA, Jitter and so on. You can use VRRP protocol to switch the traffic
flow from LAN to different SD-WAN routers and the IPSEC/GRE tunnel will
originate from one SD-WAN to another SD-WAN router based upon the traffic flow
which control instructs.
The
controller basically here are in cluster and they also carry the zero trust
policy. Here in Viptela SD-WAN controller, you have 3 types of controller in
cluster and they are VBond, VSmart and VManage.
Conclusion
Since the
approach in the LAN and WAN are same to automate the network by pushing the
policies and control from the controller. The other main feature which both
solutions have Application visibility and control. You can troubleshoot and
understand path by path for the resolution of the problem.
Making full
swing of the solution with the security, segmentation in LAN, WAN you can also
make Cisco Umbrella in your DNS queries onto the internet which can be first
layer of defense and help to protect the network from the external malicious
websites and block instantly. Cisco Umbrella is backed with the huge brain of
Talos.
May be the
next step to get the integration of the LAN and WAN is to put all the
capabilities of the controller cluster ( VBond, VSmart and Vmanage) into the DNA-Center and this DNA-Center will act as a controller for WAN and LAN networks.