Cisco ASA 5508-X VPN/IPSEC with BGP Tunnel
Today I am going to talk about the configuration example showing Cisco ASA VPN/IPsec with BGP. We will discuss Border Gateway Protocol (BGP) neighbor over an IPsec site-to-site VPN tunnel between a Cisco Adaptive Security Appliance (ASA).
Let’s take an example with the following design guide where we have Cisco ASA 5508-X as a Local ASA and Cisco ISR 4431 router as a remote router. We are going to configure the IPsec tunnel between these two devices with BGP. Remote end router Cisco ISR 4431 is in AS-200 while Cisco ASA 5508-X is in AS-100.
First, we are going to configure Cisco ASA 5508-X on the local side and then we will configure the remote router Cisco ISR 4431.
Configuration on Cisco ASA 5508-X as a Local ASA
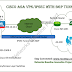
Below is the topology showing the connectivity between Cisco ASA 5508-X Firewall and Cisco ISR 4431 router over the internet cloud. The IP addresses uses here in this example is just for the example and has no relevance with any of the enterprise networks.
 |
| Fig 1.1- Cisco ASA IPSEC with BGP Tunnel |
Step-1: Configure the inside and outside interfaces on Cisco ASA 5508-X
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 200.10.10.1 255.255.255.0
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 172.16.20.1 255.255.255.0
!
Step-2: Now configure BGP configuration on Local ASA (Cisco ASA 5508-X)
!
router bgp 200
bgp log-neighbor-changes
address-family ipv4 unicast
neighbor 197.10.10.1 remote-as 100
neighbor 197.10.10.1 description Remote Router
neighbor 197.10.10.1 ebgp-multihop 255
neighbor 197.10.10.1 activate
network 172.16.20.0 mask 255.255.255.0
no auto-summary
no synchronization
exit-address-family
!
route outside 198.51.100.0 255.255.255.0 203.0.113.2 1
!
access-list outside_cryptomap permit ip host 200.10.10.1 host 197.10.10.1
!
Step-3: Phase 1 Configuration which uses isakmp policy 300
!
crypto ikev1 policy 300
authentication pre-share
encryption 3des
hash md5
group 5
lifetime 86400
!
tunnel-group 197.10.10.1 type ipsec-l2l
tunnel-group 197.10.10.1 ipsec-attributes
ikev1 pre-shared-key cisco123
!
crypto ikev1 enable outside
!
Step-4: Phase 2 Configuration
!
crypto ipsec ikev1 transform-set TSET esp-3des esp-sha-hmac
crypto map outside_map 1 match address outside_cryptomap
crypto map outside_map 1 set peer 197.10.10.1
crypto map outside_map 1 set ikev1 transform-set TSET
crypto map outside_map interface outside
!
Configuration on Cisco ISR 4431 as a Remote router
Step-1: Phase 1 Configurations
!
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 5
crypto isakmp key cisco123 address 200.10.10.1 255.255.255.0
!
Step-2: Phase 2 Configurations
!
crypto ipsec transform-set TSET esp-3des esp-sha-hmac
crypto map CMAP 10 ipsec-isakmp
set peer 200.10.10.1
set transform-set TSET
match address VPN
!
interface Loopback0
ip address 172.16.30.1 255.255.255.0
!
interface FastEthernet0/0
ip address 197.10.10.1 255.255.255.0
duplex auto
speed auto
crypto map CMAP
!
Step-3: BGP Configuration
!
router bgp 100
no synchronization
bgp log-neighbor-changes
network 172.16.30.0 mask 255.255.255.0
neighbor 200.10.10.1 remote-as 200
neighbor 200.10.10.1 ebgp-multihop 255
no auto-summary
!
ip route 0.0.0.0 0.0.0.0 198.51.100.2
!
ip access-list extended VPN
permit ip host 197.10.10.1 host 200.10.10.1
!