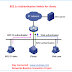
Enabling 802.1X Authentication on Switch
As many of you already know about the 802.1X. 802.1X port-based authentication as a client-server based access control and
authentication protocol that limits unauthorized clients from joining to a LAN
through publicly available ports. An authentication server authenticates each
supplicant (client) linked to an authenticator (network access switch) port
before making accessible any services offered by the switch or the LAN.
802.1X support needs an authentication server that is provisioned
for Remote Authentication Dial-In User Service (RADIUS). 802.1X authentication
does not work if the network access switch can route packets to the configured
authentication RADIUS server. To verify that the switch can route packets, you
must ping the server from the switch.
Fig 1.1- 802.1x Authentication on Switch
|
Enabling 802.1X Authentication
To enable 802.1X port-based authentication, you first
must enable 802.1X globally on your Switch, then enable AAA and specify the
authentication method list. A method list describes the sequence and
authentication methods that must be queried to authenticate a user.
To disable 802.1X authentication, use the dot1x
port-control force-authorized or the no dot1x port-control interface
configuration command.
Below is the basic example shows how to enable AAA and 802.1X on Fast Ethernet port 1/1
RouteXP_Switch# configure terminal
RouteXP_Switch(config)# dot1x system-auth-control
RouteXP_Switch(config)# aaa new-model
RouteXP_Switch(config)# aaa
authentication dot1x default group radius
RouteXP_Switch(config)# interface fastethernet1/1
RouteXP_Switch(config-if)# dot1x port-control auto
RouteXP_Switch(config-if)# end