Cisco Router as Zone Based Firewall functionality
Today I am going to talk about the use of the Cisco router which as IOS or IOS-XE device with Zone Based Firewall functionality. In order to configure the IOS or IOS-XE device and it is assumed that we have already configured the L2L VPN or DMVPN between the endpoints.
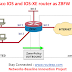
In the below example I have a local subnet 7.7.7.0/24 that is configured on Loopback1 of the ISR that would like to reach the remote subnet of 8.8.8.0/24 that resides behind an ASA. This traffic is being encrypted via IKEv1 site-to-site tunnel.
Note : The subnet and the IP used here is for the demo purposes and has no relevance with any of the enterprise network.
In the below example I have a local subnet 7.7.7.0/24 that is configured on Loopback1 of the ISR that would like to reach the remote subnet of 8.8.8.0/24 that resides behind an ASA. This traffic is being encrypted via IKEv1 site-to-site tunnel.
Note : The subnet and the IP used here is for the demo purposes and has no relevance with any of the enterprise network.
 |
| Fig 1.1- Cisco IOS and IOS-XE as ZBFW |
When thinking about ZBFW with the "self" zone configured consider the router as two different traffic types.
1.) traffic that is destined TO the box
2.) traffic that is destined THROUGH the box
Through the box traffic is handled normally in regards to ZBFW. Configure the traffic to be inspected/passed between two interfaces and apply that to the zone-pair accordingly.
To the box traffic can be handled differently in regards to ZBFW, especially when the to the box traffic is VPN traffic. If the self zone is not called inside of your zone-pair security configuration, by default all traffic is allowed. When the self zone is configured and there is no zone-pair configure, all traffic is denied.
When to use inspect or pass?
This is all dependant on the needs of the environmnet.
Does the router only respond to VPN traffic? Then only inspect from the outside zone to the self zone.
Does the router only initiate VPN traffic? Then only inspect from the self zone to the outside zone.
Does the router to act as both initiator and responder? Then configure either pass or inspect, also configure both self to outside and outside to self zone policies.
Configure ZBFW (pass action)
I. Complete these steps in order to configure the ZBFW for THROUGH the box traffic
Configure the traffic that is going to traverse THROUGH the router:
RouteXP_4331(config)#access-list 100 permit ip 7.7.7.0 0.0.0.255 8.8.8.0 0.0.0.255
Configure the zone member interfaces
RouteXP_4331(config)#zone security inside
RouteXP_4331(config)#zone security outside
Configure the class-map that is going to match the previously configured THROUGH the router traffic:
RouteXP_4331(config)# class-map type inspect match-any IN-->OUT_CMAP
RouteXP_4331(config-cmap)# match access-group 100
Configure the policy-map that is going to take action on the previously configured class-map:
RouteXP_4331(config-cmap)# policy-map type inspect IN-->OUT_PMAP
RouteXP_4331(config-pmap)# class IN-->OUT_CMAP
RouteXP_4331(config-pmap-c)# inspect
Configure the zone-pair security that will tie the two previously configured zone member interfaces (step 2) to the previously configured policy-map:
RouteXP_4331(config-cmap)# zone-pair security IN-->OUT source inside destination outside
RouteXP_4331(config-sec-zone-pair)# service-policy type inspect IN-->OUT_PMAP
II. Complete these steps in order to configure the ZBFW for the VPN to/from the box traffic
Configure the traffic that is going to traverse to/from the router
RouteXP_4331(config)#ip access-list extended 101
RouteXP_4331(config-ext-nacl)# permit udp any any eq isakmp
RouteXP_4331(config-ext-nacl)# permit udp any any eq non500-isakmp
RouteXP_4331(config-ext-nacl)# permit esp any any
Configure the class-map that is going to match the previously configured to/from the router traffic:
RouteXP_4331(config)#class-map type inspect match-any SELF-->OUT_CMAP
RouteXP_4331(config-cmap)# match access-group 101
RouteXP_4331(config-cmap)# class-map type inspect match-any OUT-->SELF_CMAP
RouteXP_4331(config-cmap)# match access-group 101
Configure the policy-map that is going to take action on the previously configured class-map:
RouteXP_4331(config-cmap)# policy-map type inspect SELF-->OUT_PMAP
RouteXP_4331(config-pmap)# class SELF-->OUT_CMAP
RouteXP_4331(config-pmap-c)# pass
*** NOTE: Since we are "pass"ing this traffic this action is unidirectional and will need the subsequent "pass" action from "outside" to "self" ***
RouteXP_4331(config)# policy-map type inspect OUT-->SELF_PMAP
RouteXP_4331(config-pmap)# class OUT-->SELF_CMAP
RouteXP_4331(config-pmap-c)# pass
Configure the zone-pair security that will tie the two previously configured zone member interfaces (step 2) to the previously configured policy-map
RouteXP_4331(config-cmap)# zone-pair security SELF-->OUT source self destination outside
RouteXP_4331(config-sec-zone-pair)# service-policy type inspect SELF-->OUT_PMAP
RouteXP_4331(config-sec-zone-pair)# zone-pair security OUT-->SELF source outside destination self
RouteXP_4331(config-sec-zone-pair)# service-policy type inspect OUT-->SELF_PMAP
Apply the previously configured zone member (step 2) to the interfaces
RouteXP_4331(config-sec-zone-pair)# interface loopback1
RouteXP_4331(config-if)# zone-member security inside
RouteXP_4331(config-if)# interface g0/0/1
RouteXP_4331(config-if)# zone-member security outside
Configure ZBFW (inspect action)
Follow the aforementioned steps titled "Complete these steps in order to configure the ZBFW for THROUGH the box traffic". Once completed follow the below steps in regards to the IKE traffic that is destined to/from the router
Configure the traffic that is going to traverse to/from the router
RouteXP_4331(config)#ip access-list extended 101
RouteXP_4331(config-ext-nacl)# permit udp any any eq isakmp
RouteXP_4331(config-ext-nacl)# permit udp any any eq non500-isakmp
RouteXP_4331(config-ext-nacl)# permit esp any any
Configure the class-map that is going to match the previously configured to/from the router traffic
RouteXP_4331(config)#class-map type inspect match-any SELF-->OUT_CMAP
RouteXP_4331(config-cmap)# match access-group 101
RouteXP_4331(config-cmap)# class-map type inspect match-any OUT-->SELF_CMAP
RouteXP_4331(config-cmap)# match access-group 101
Configure the policy-map that is going to take action on the previously configured class-map
RouteXP_4331(config-cmap)# policy-map type inspect SELF-->OUT_PMAP
RouteXP_4331(config-pmap)# class SELF-->OUT_CMAP
RouteXP_4331(config-pmap-c)# inspect
*** NOTE: If we only configure the above "inspect" action, the router would only act as the initiator of the flow. Subsequently if the remote device initiated the tunnel, the router would deny this flow as he does not have the below policy-map configured ***
RouteXP_4331(config)# policy-map type inspect OUT-->SELF_PMAP
RouteXP_4331(config-pmap)# class OUT-->SELF_CMAP
RouteXP_4331(config-pmap-c)# inspect
*** NOTE: When we configure the router to "inspect" both OUT-->SELF and SELF-->OUT, the router now can act as both initiator and responder. If you would to only respond only configure the OUT-->SELF policy-map ***
Configure the zone-pair security that will tie the two previously configured zone member interfaces (step 2) to the previously configured policy-map:
RouteXP_4331(config-cmap)# zone-pair security SELF-->OUT source self destination outside
RouteXP_4331(config-sec-zone-pair)# service-policy type inspect SELF-->OUT_PMAP
RouteXP_4331(config-sec-zone-pair)# zone-pair security OUT-->SELF source outside destination self
RouteXP_4331(config-sec-zone-pair)# service-policy type inspect OUT-->SELF_PMAP
Apply the previously configured zone member (step 2) to the interfaces:
RouteXP_4331(config-sec-zone-pair)# interface loopback1
RouteXP_4331(config-if)# zone-member security inside
RouteXP_4331(config-if)# interface g0/0/1
RouteXP_4331(config-if)# zone-member security outside