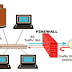
Next Generation Firewalls Comparison Analysis
This article is based upon the analysis done on various Next Generation Firewalls from different vendors. In order to determine the relative security effectiveness of devices on the market and facilitate accurate product
comparisons, there are some factors taken into considerations for all these next generation firewalls.
Fig 1.1 - Network Firewall
|
So if we are talking about the factors as per the Gartner says about Next Generation Firewall, we can take it as
- Inbuilt NGIPS- Next Generation IPS
- Stability
- Reliability
- Security effectiveness
These factors are very important factors for the next generation firewall and for the testing of the NGFW products the devices are deployed using the default or recommended policy as provided by
the vendor.This provides readers with the most useful information on key NGFW security effectiveness and performance
capabilities based upon their expected usage.
Lets start with the features for all the vendors. The vendors i am including here are
- Barracuda Firewalls
- Check Point
- Cisco NGFW
- Cyberoam
- Dell SonicWALL
- Fortinet
- McAfee
- Palo Alto Networks
- WatchGuard
Bypassing information from security devices by any means is conceal and modifying attacks in order to avoid detection and blocking by
security products. Resistance to bypass security devices are a critical component in an NGFW. If a single evasion is missed, an
attacker can utilize an entire class of exploits to circumvent the NGFW, rendering it virtually useless. Many of the
techniques used in this test have been widely known for years and should be considered minimum requirements
for the NGFW product category, while others are more recent. This particular category of tests is critical in the final
weighting with regard to product guidance.
Fig 1.2- Firewall Comparison
|
An NGFW should be able to identify users and groups and apply security policy based on identity. Where possible,
this should be achieved via direct integration with existing enterprise authentication systems (such as Active
Directory) without the need for custom server-side software. This allows the administrator to create even more
granular policies.
Security effectiveness testing leverages the deep expertise of Security engineers to generate the same types of
attacks used by modern cybercriminals, utilizing multiple commercial, open-source, and proprietary tools as
appropriate. With over 1800 live exploits, this is the industry’s most comprehensive test to date. Most notable, all
of the live exploits and payloads in these tests have been validated such that:
- Reverse shell is returned
- Bind shell is opened on the target, allowing the attacker to execute arbitrary commands
- Malicious payload is installed
- System is rendered unresponsive
Exploits can be initiated either locally by the target (desktop client) or remotely by the attacker against a server.
Since 2007, Researchers have noticed a dramatic rise in the number of client-side exploits, as these can be
easily launched by an unsuspecting user who visits an infected website. At first , IPS products did not focus on
these types of attacks, which were deemed to be the responsibility of antivirus products.
This approach is no longer viewed as acceptable and, despite the difficulty of providing extensive coverage for client-side attacks, the IPS (and NGFW) industry has attempted to provide more complete client-side coverage. This is particulary important for NGFW devices, which are typically used to protect client desktops rather than data centers and servers; the latter comprise deployment scenarios where separate, dedicated firewall and IPS devices are more common.
The security effectiveness of the IPS component of the NGFW can be seen in the following table as factors in
evasions to the exploit block rate
Fig 1.3- Security Effectiveness (IPS)
|
Finally, the overall security effectiveness of the NGFW is determined using the formula in figure 1. Here combines scores relating to firewall security effectiveness, IPS security effectiveness, and stability and reliability in
order to generate a combined security effectiveness score for the NGFW device.
Fig 1.4- Security Effectiveness (NGFW)
|
Long-term stability is particularly important for an in-line device, where failure can produce network outages.
These tests verify the stability of the DUT along with its ability to maintain security effectiveness while under
normal load and while passing malicious traffic.