Introduction to Cisco ASA Zone-Based Firewall
Cisco ASA Zone-Based Firewall that offers network security and traffic control. It works on the basis of security zones, where each zone represents a security level and may be assigned unique traffic control regulations.
Cisco Zone-Based Firewall is a Firewall architecture that uses security zones to define trust levels and control network traffic. The zone-based Firewall uses a modular policy-based approach, which allows for easy and flexible configuration of security policies.
The Firewall analyses traffic that crosses from one zone to another and allows or refuses it depending on security criteria.
Zone-Based Firewall is a scalable and adaptable network security solution that may be used in conjunction with other security features such as access control lists (ACLs) and VPNs.
To design a Zone-Based Firewall, you must define security zones, assign interfaces to zones, and write policies that indicate how traffic between zones is allowed or refused.
In a zone-based Firewall, each network segment is assigned to a specific security zone, and traffic between zones is regulated by a security policy. The security policies define what traffic is allowed and what traffic is blocked.
We may specify security zones and assign individual policies to each zone using Cisco Zone Based Firewall.
Cisco Zone-Based Firewall is implemented on Cisco IOS-based routers and Cisco ASA Firewall appliances. The Firewall provides features such as stateful packet inspection, application inspection, and URL filtering, among others.
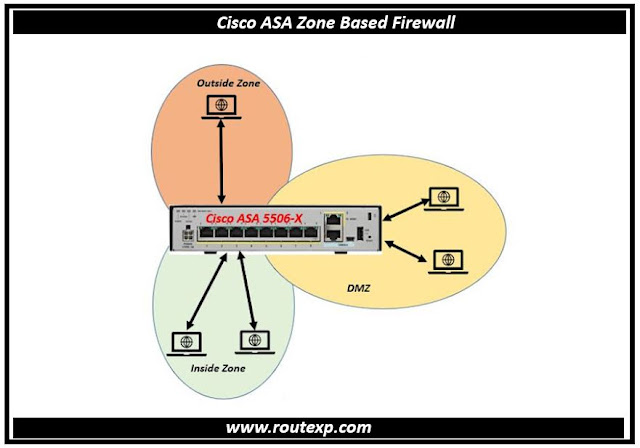
Security Zone: An interface or collection of interfaces designated as a security zone get a specific policy application. By default, all traffic within the same Security Zone is allowed.
However, all traffic outside of the same Security Zone is restricted, with the exception of that produced by the router. It is necessary to create zone-pairs and rules for each zone in order to allow traffic between security zones.
Zone-pair: We can decide on a unidirectional Firewall policy between zones using zone pairs. A zone-pair, to put it simply, chooses the direction of interesting traffic. Between the source and destination zones, the direction is defined.
Zone policy: What type of traffic should be allowed or prohibited between zones is decided by zone policy. For instance, we wish to allow HTTP traffic while blocking SMTP traffic.
The three acts under zone policy are "pass," "drop," and "inspect." Pass and Drop actions have an immediate impact on traffic, but Inspect action instructs the Firewall to filter traffic using a pre-defined class map.
Continue Reading...